Terraform Job General Troubleshooting
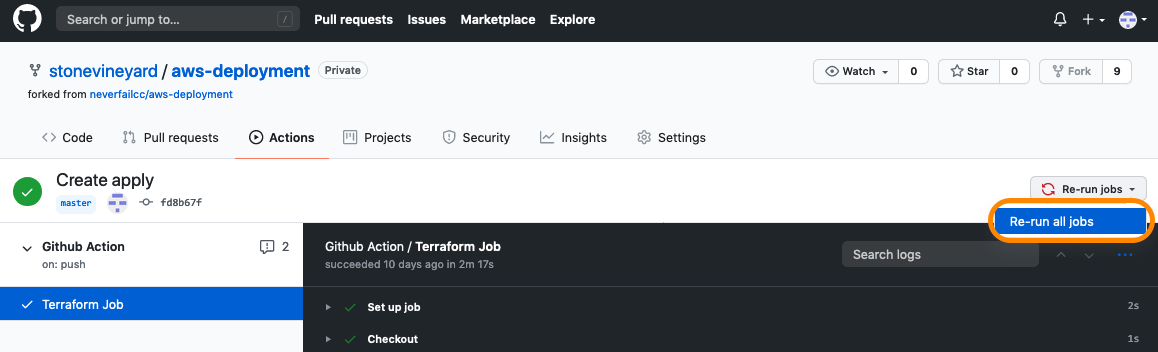
We have tried to capture and handle all possible scenarios during the infrastructure deployment, but due to the complexity of the operation, it is possible that something can go wrong. If you receive an error during the Terraform job, first, let the job complete, then afterwards, try re-running the job by clicking the Re-run jobs button on the top-right. If you still have problems, feel free to reach out to your engagement lead for assistance.