AWS Sandbox Infrastructure Deployment
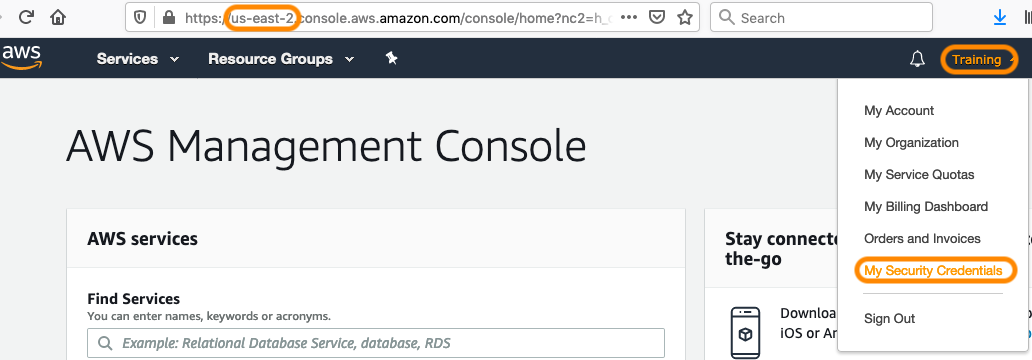
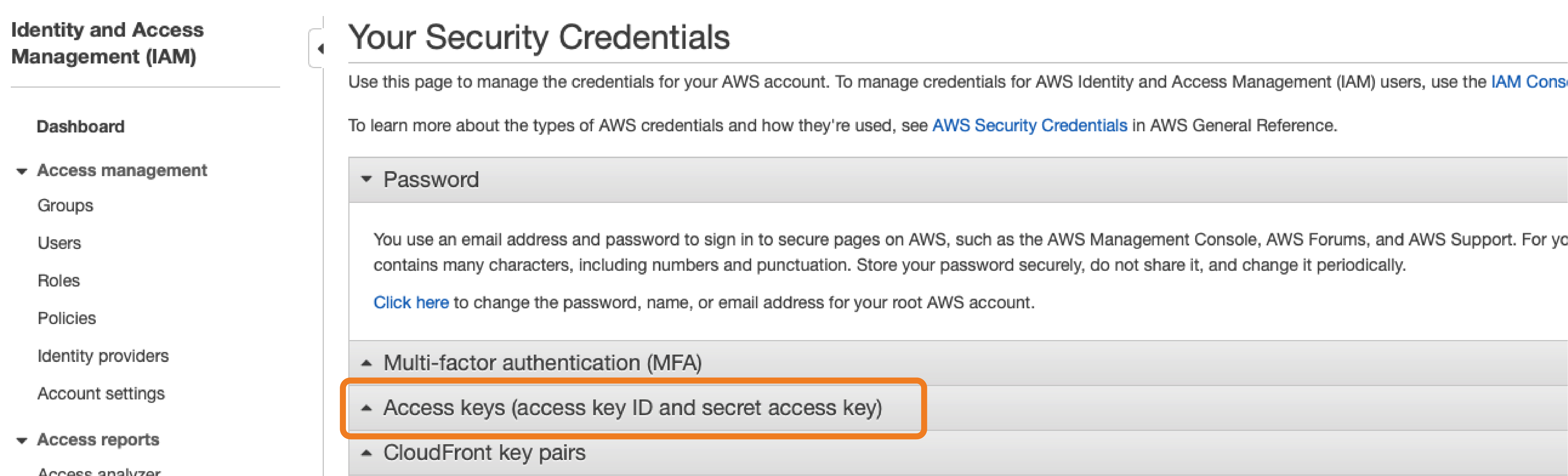
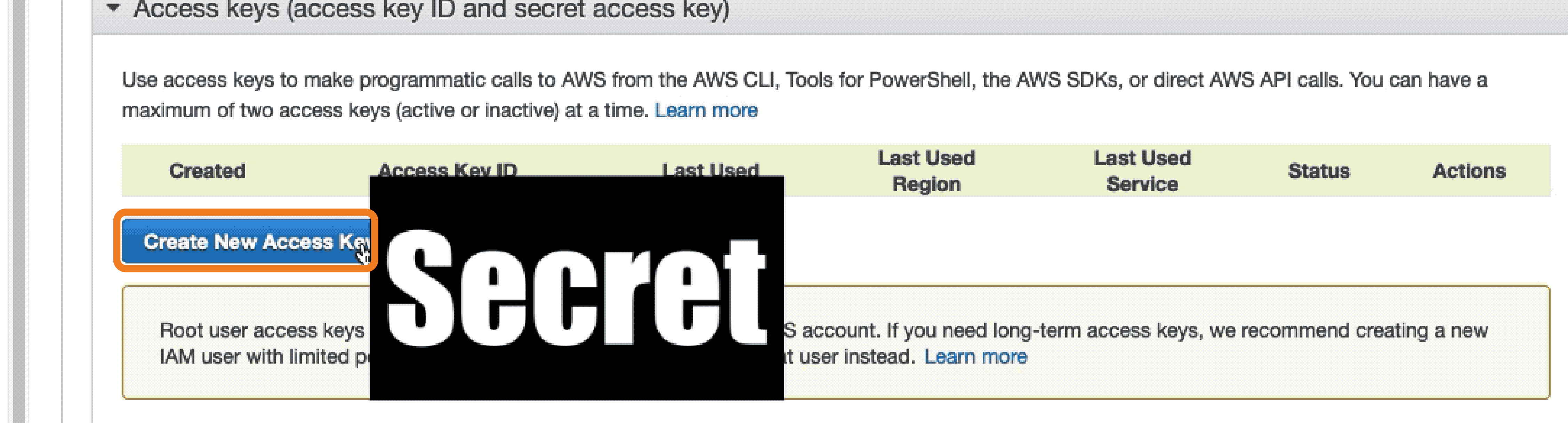
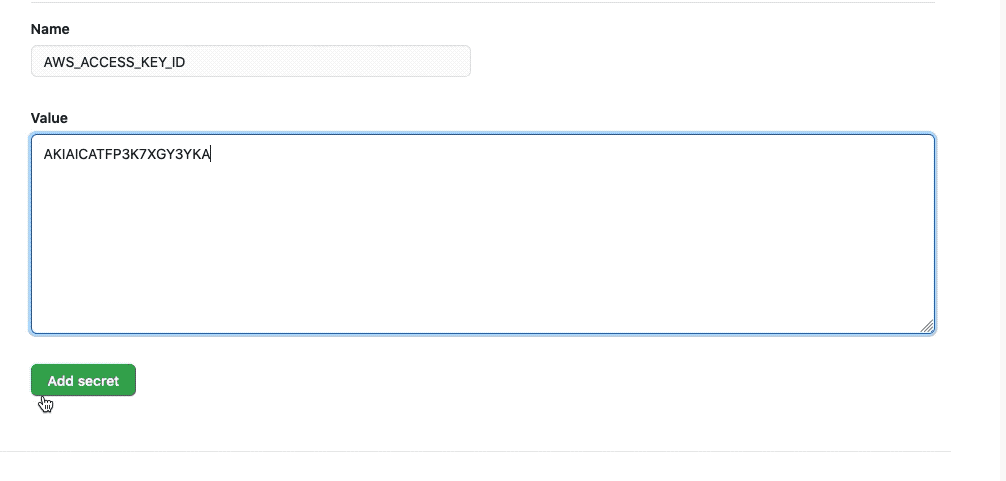
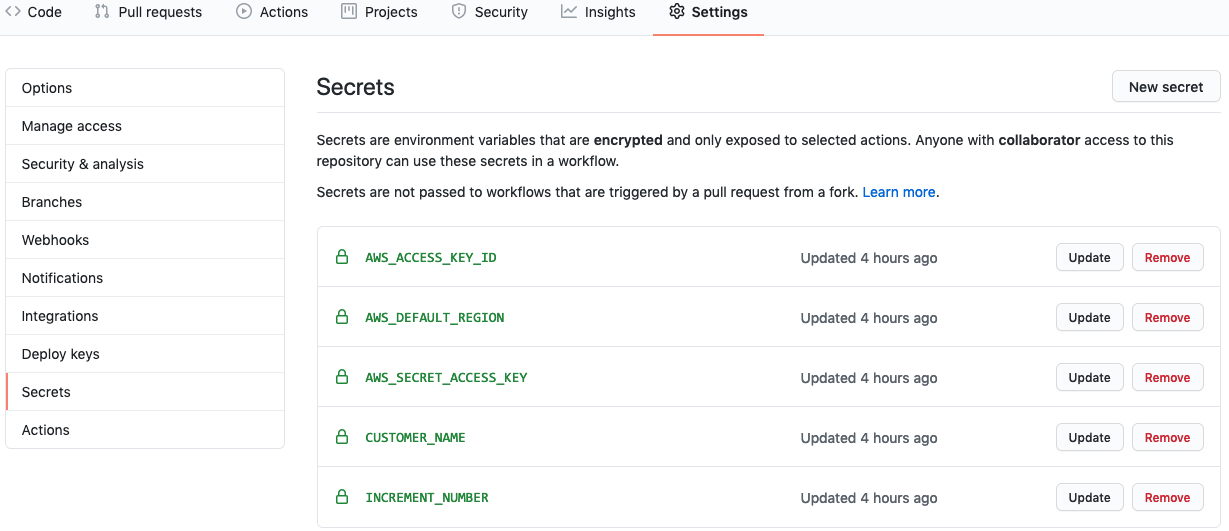
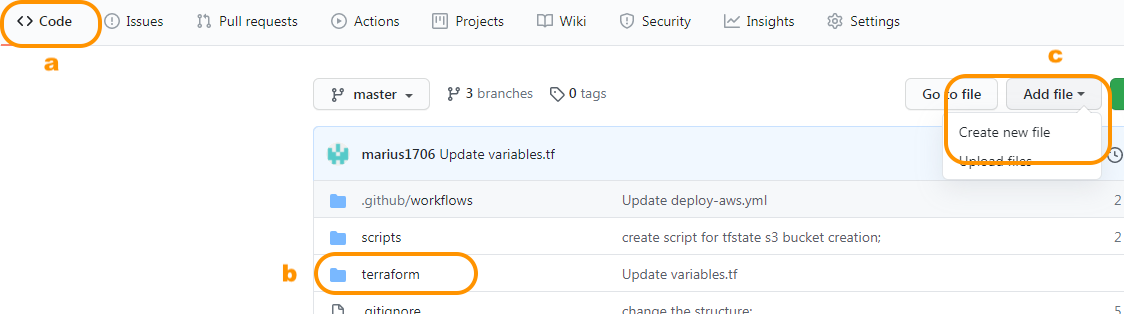
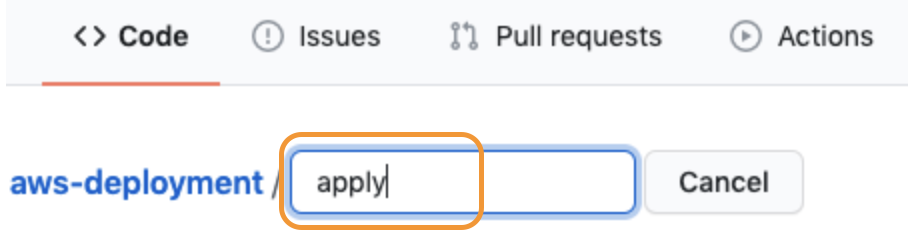
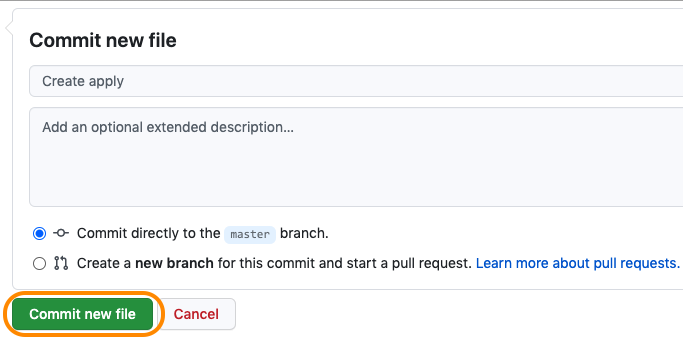
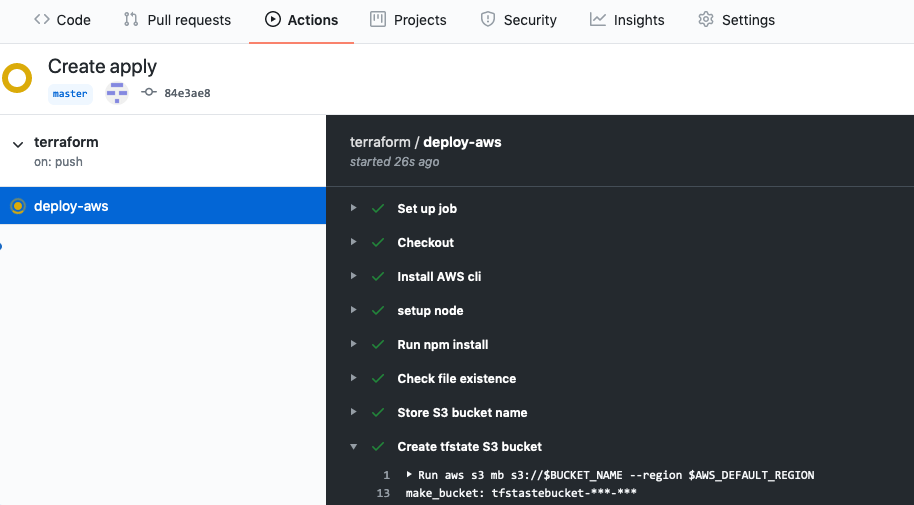
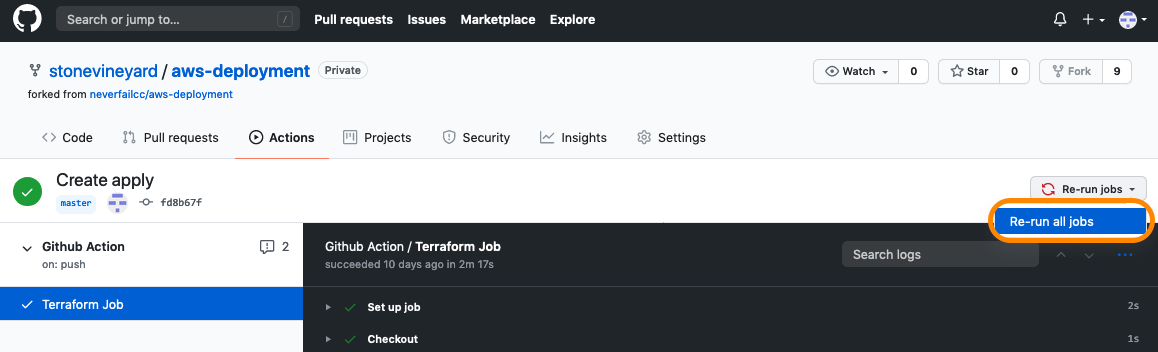
Welcome to the AWS Sandbox Infrastructure Deployment phase. Here you will be tasked to use Github Actions and Terraform to provision a set of assets needed for the deployment. The approximate time expected to complete this deployment is 20 minutes.
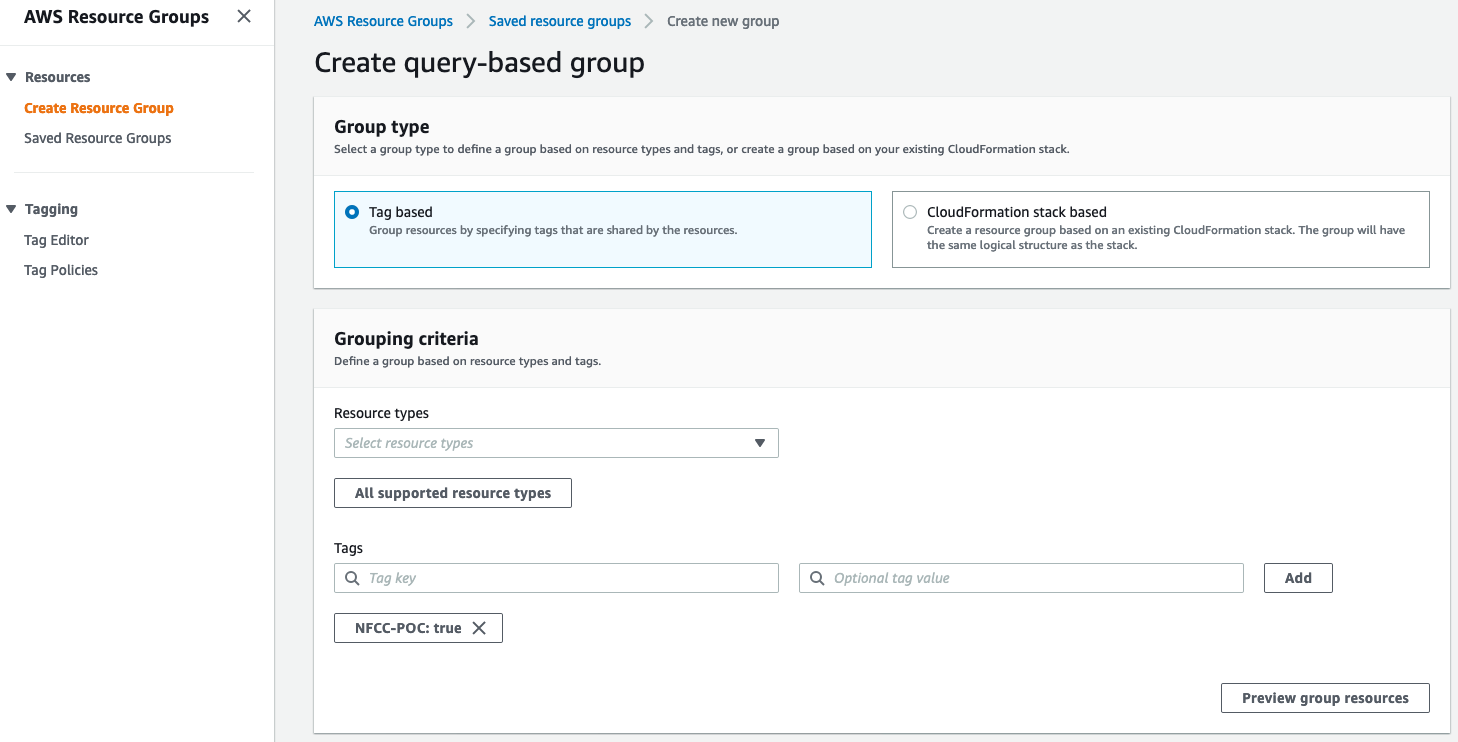
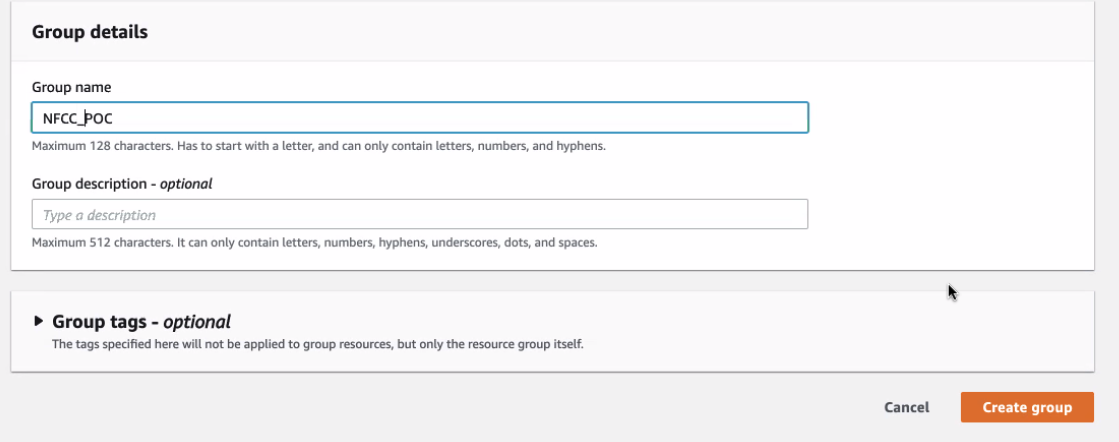
All assets created should have the NFCC-POC : true tag applied. The tags will make it easier to locate resources and to manage billing as tags can be used by AWS Cost Explorer and Cost and Usage Report.