AWS BOT Deployment
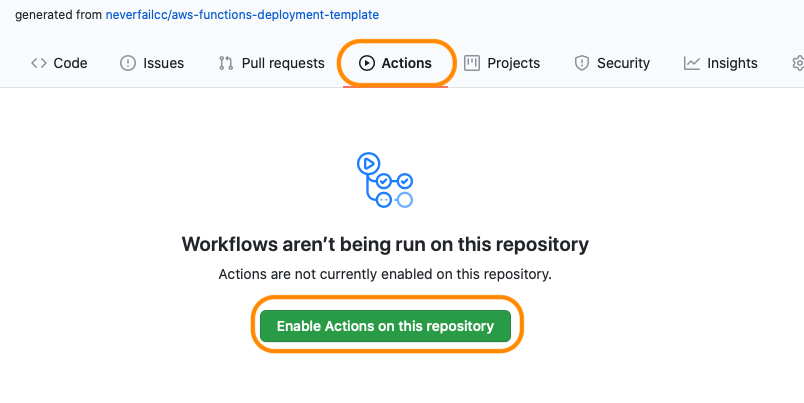
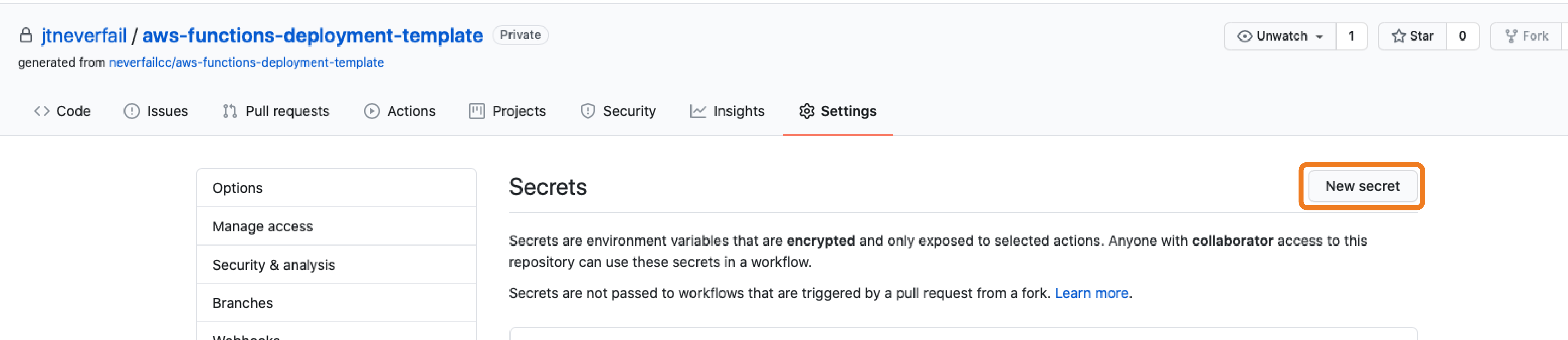
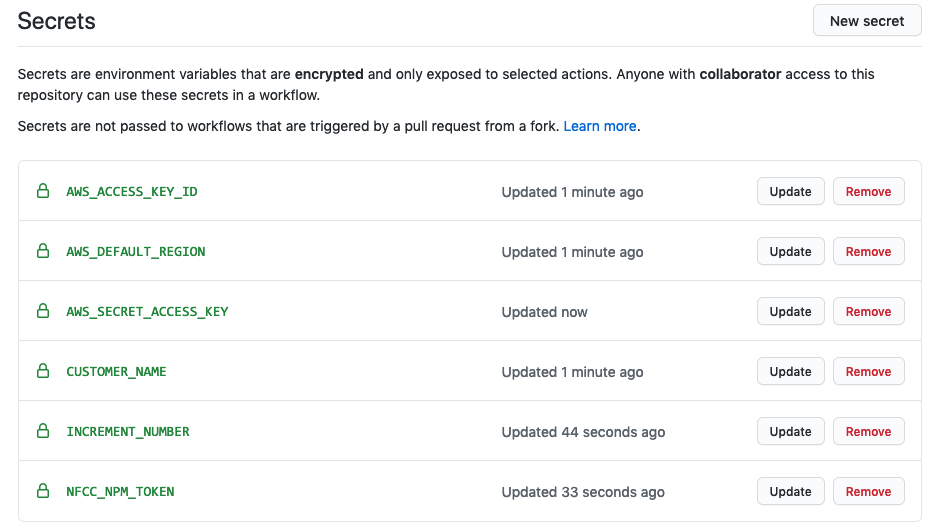
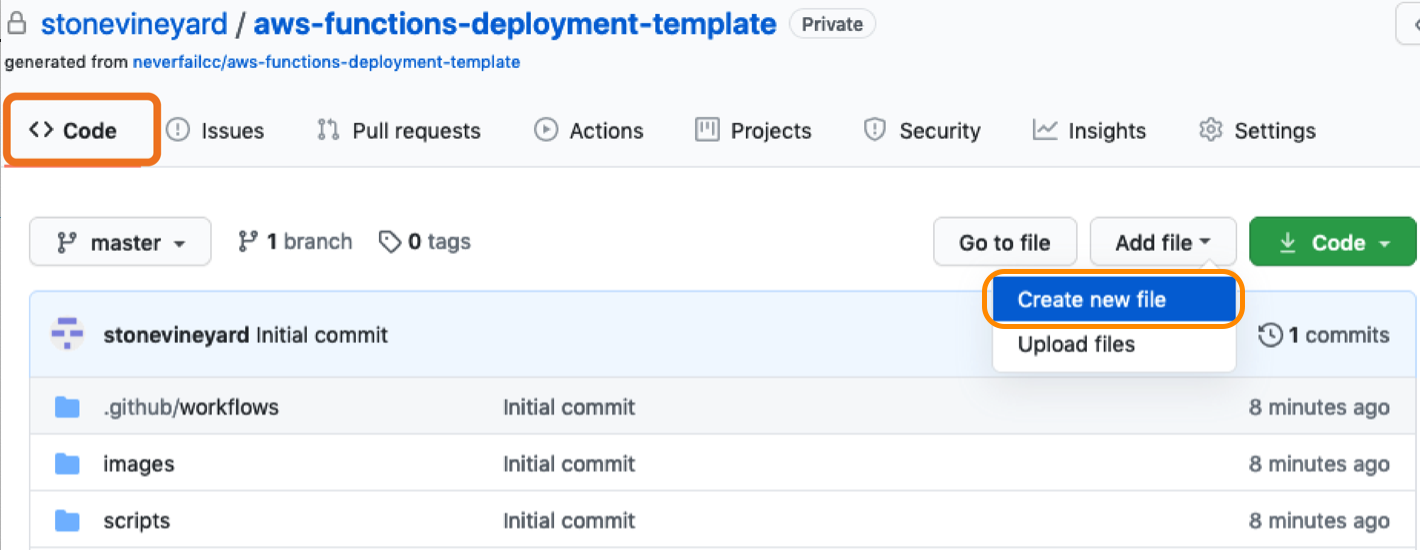
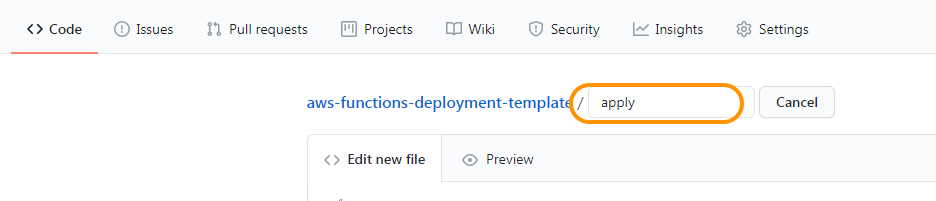
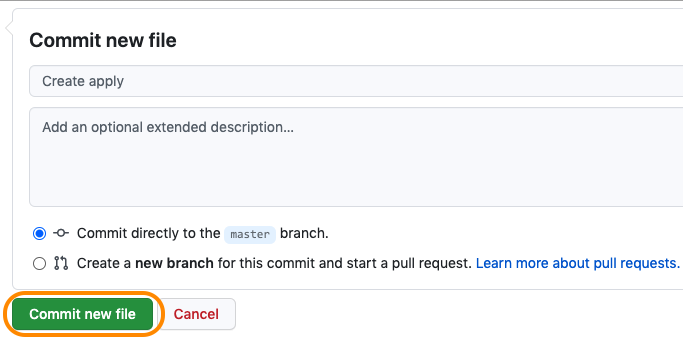
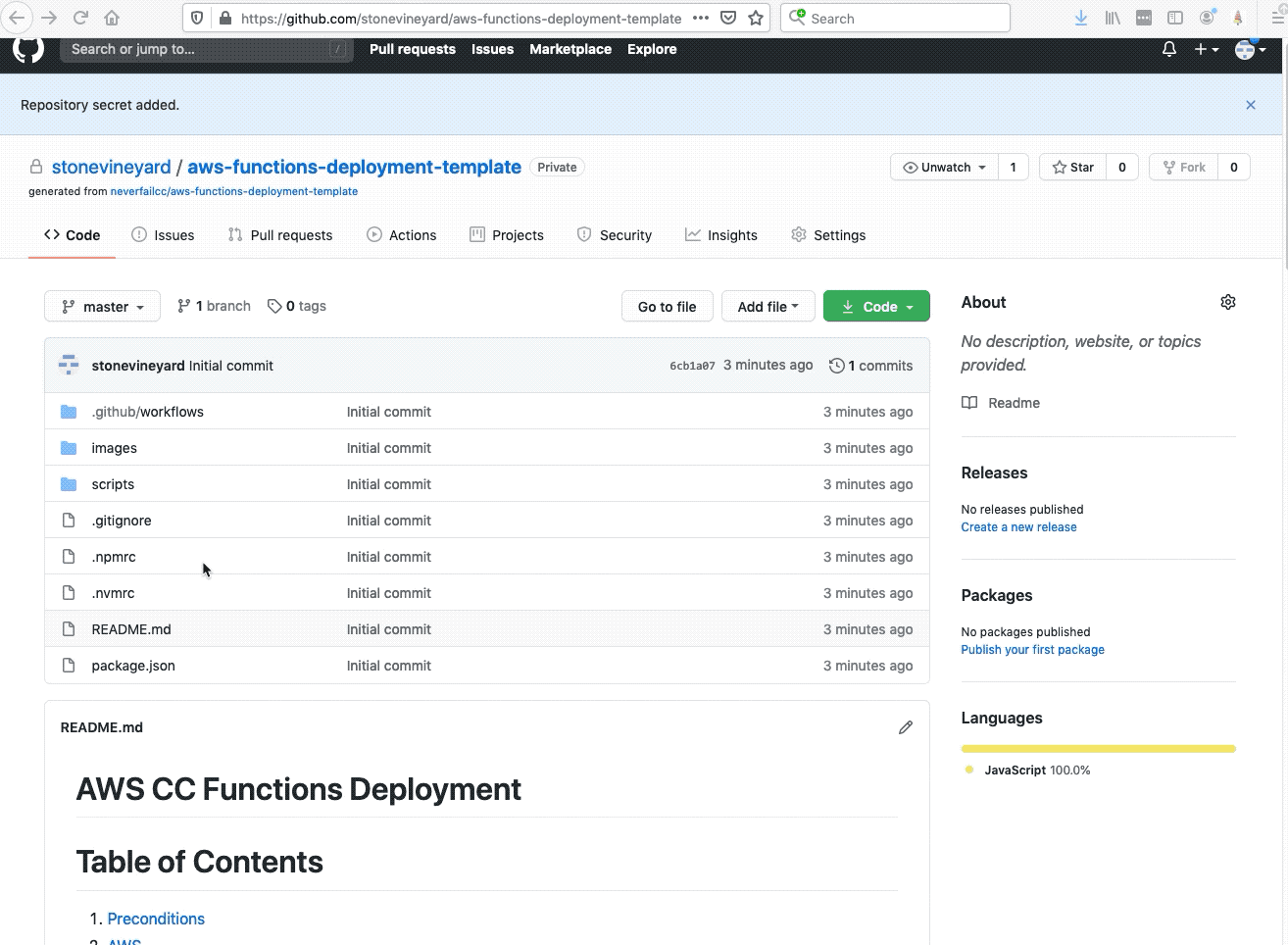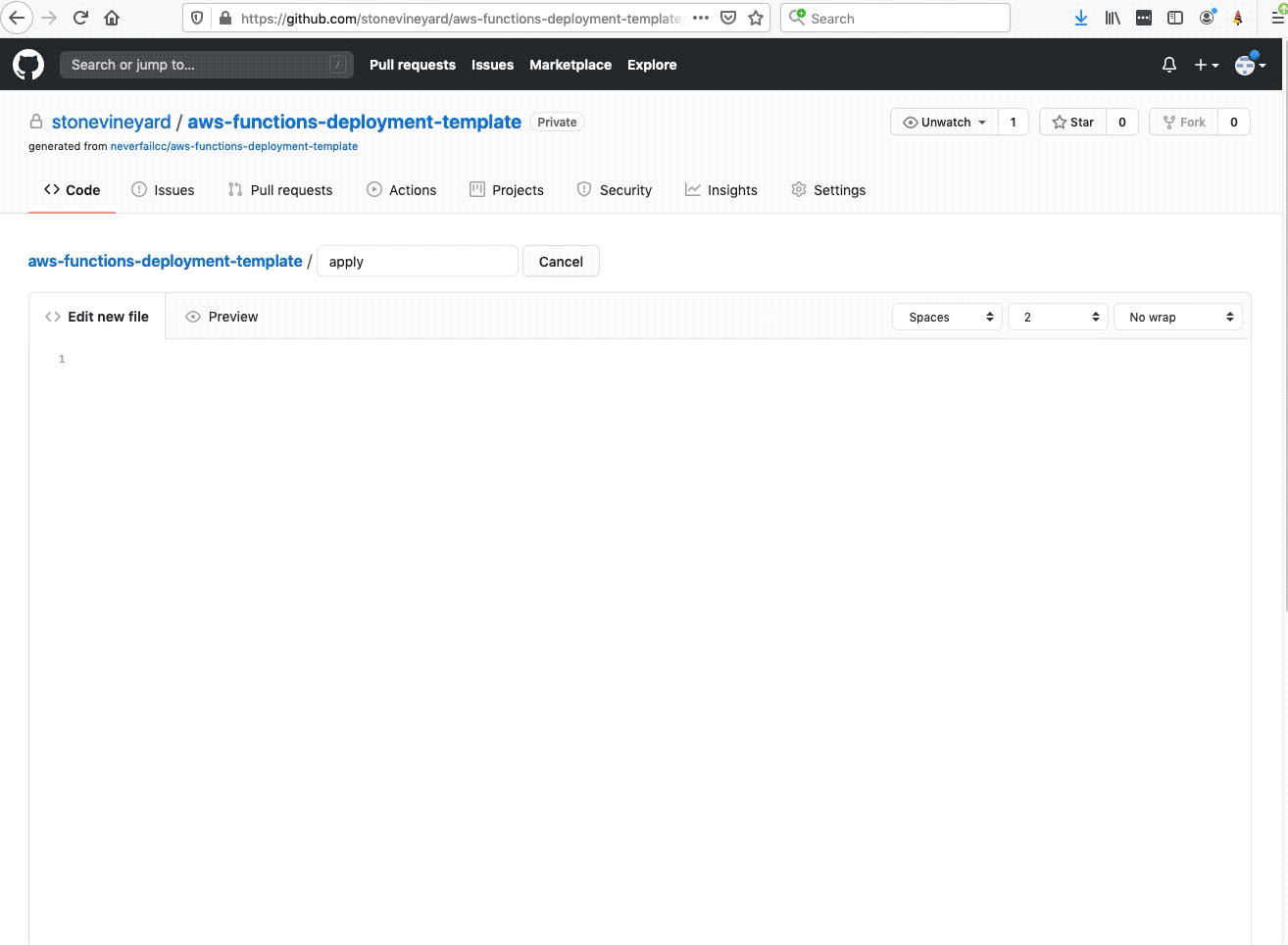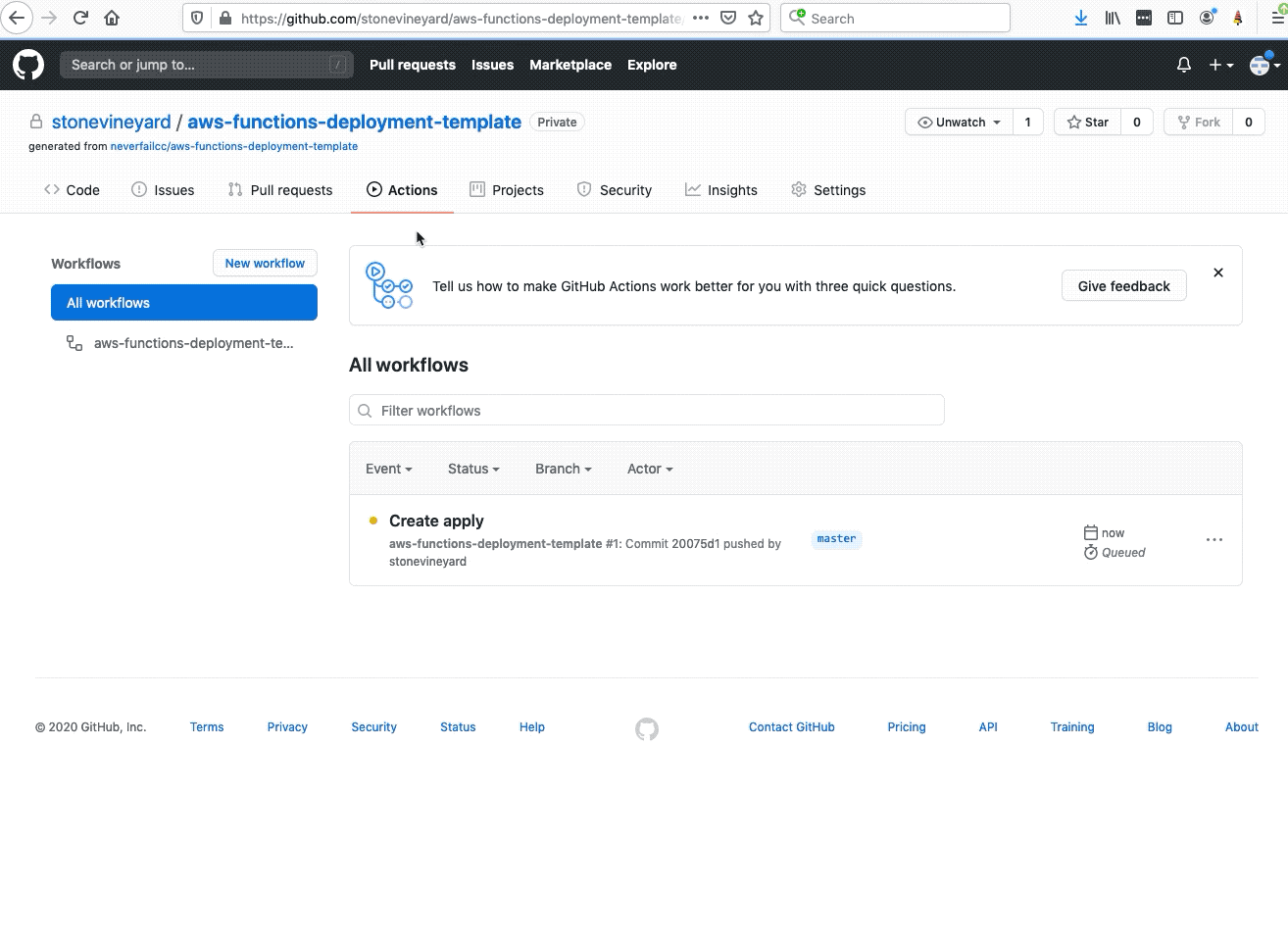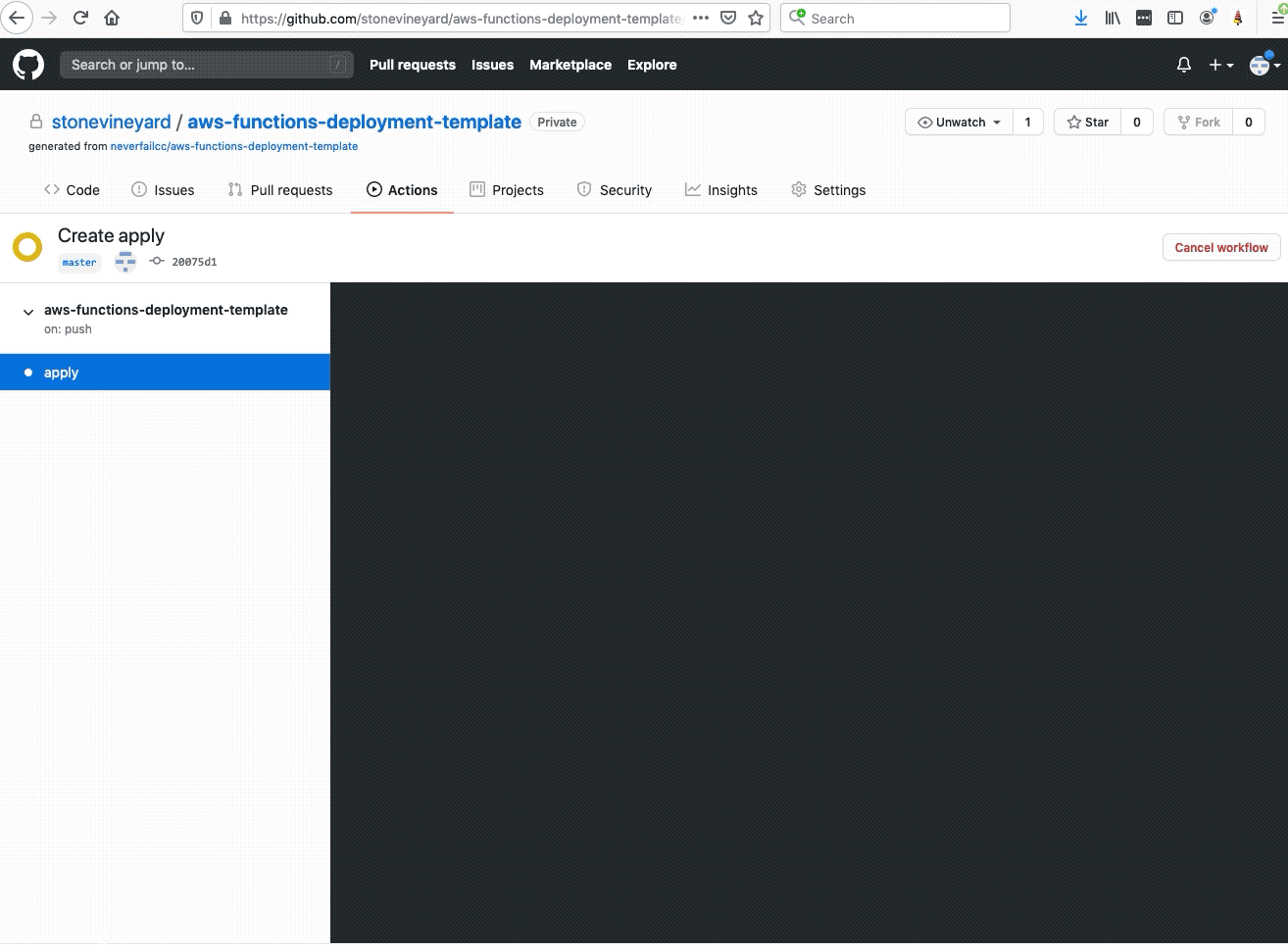
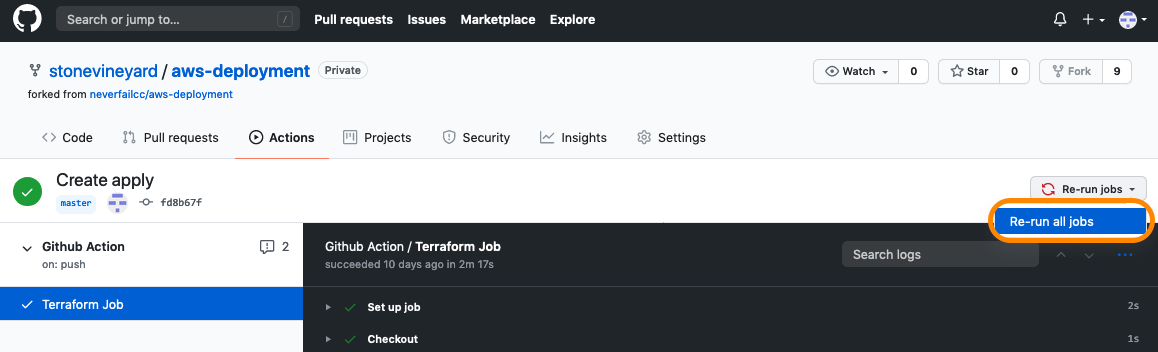
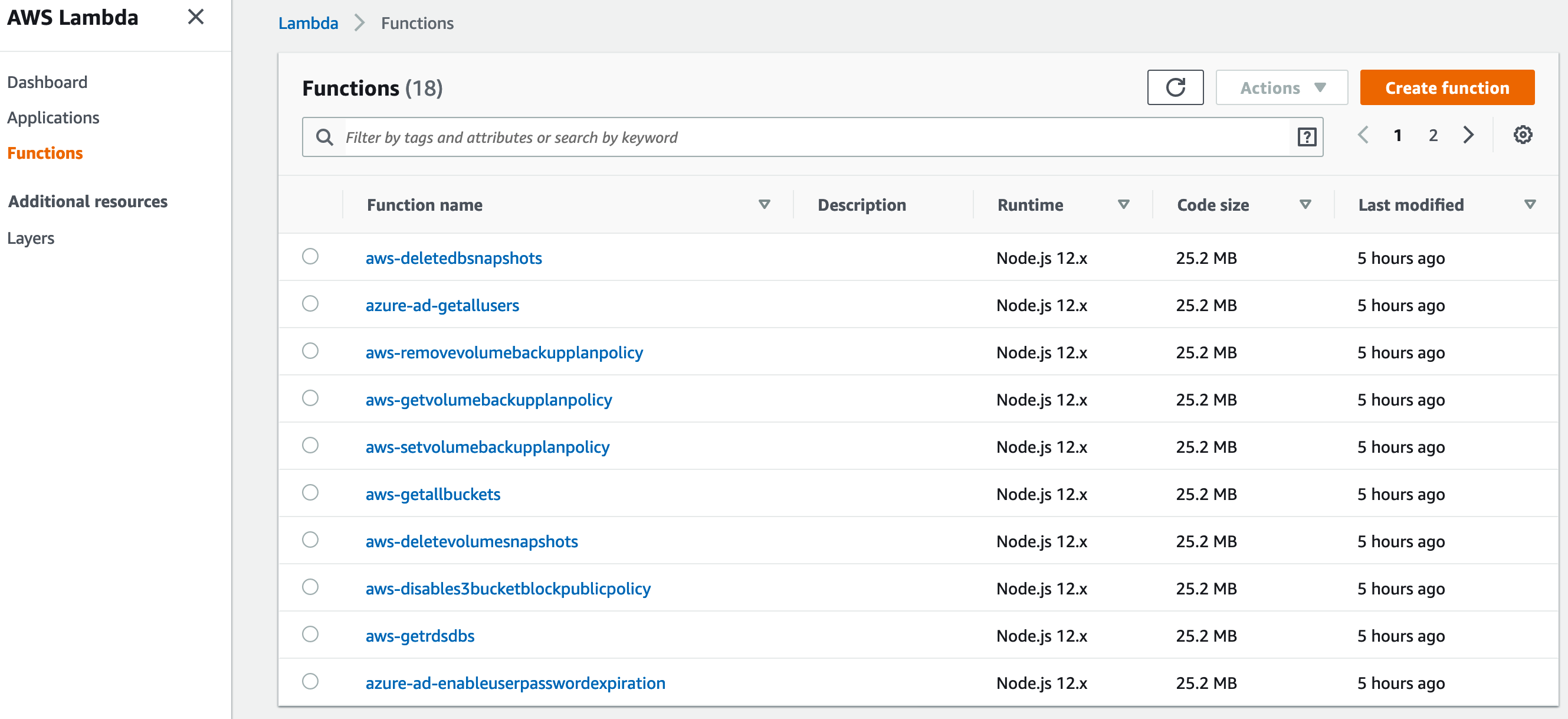
Welcome to the AWS Bot Deployment phase. Here you will be tasked to use Github Actions and Terraform to provision a set of Neverfail Continuous Controls (NFCC) functions inside your AWS Lambda service to support your deployment. After function deployment, each will be automatically registered on the NFCC platform as a customer collection bot or as a customer remediation bot.
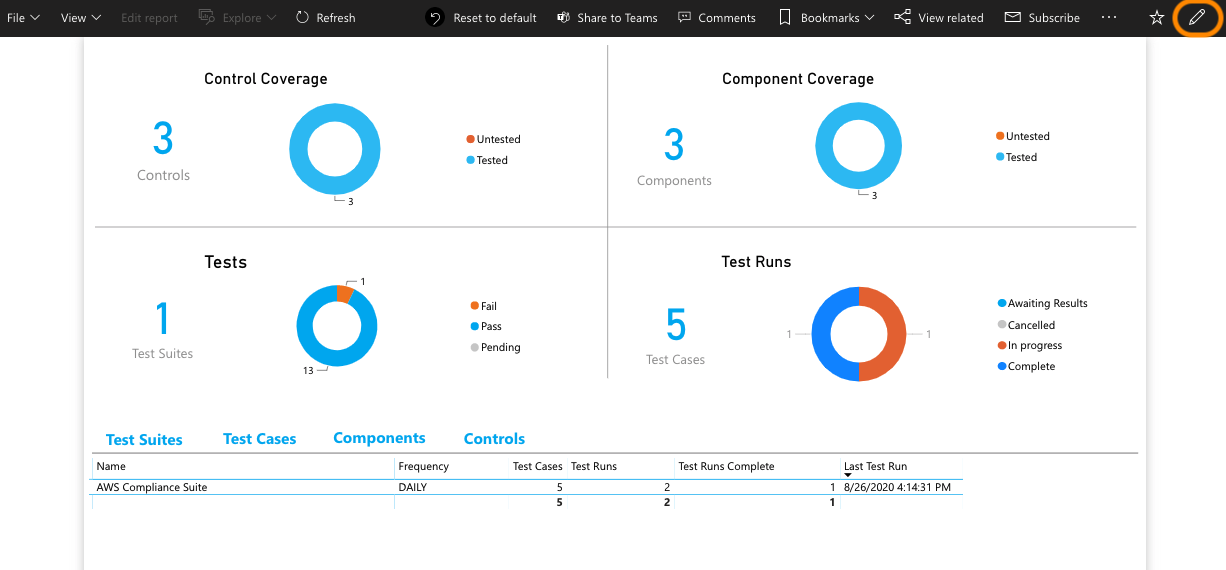
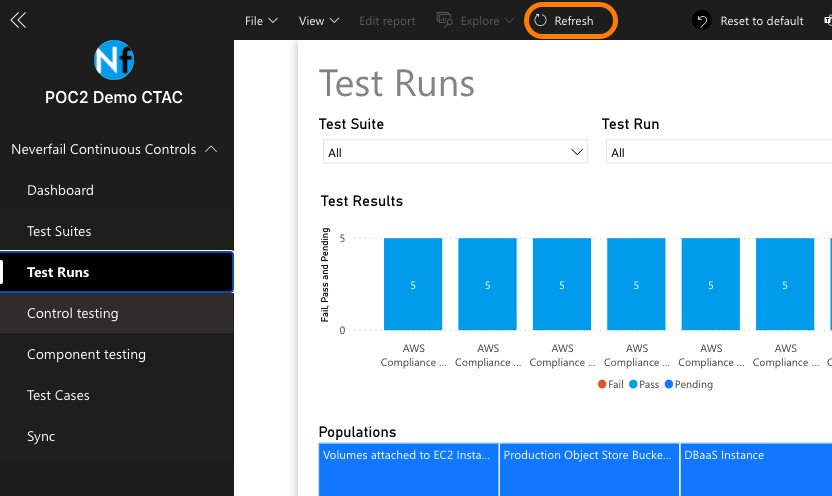
The collection bots are used to collect component (source system/application) populations and evidence from the Sandbox Deployment cloud infrastructure provisioned in the previous deployment. The customer remediation bots are used to ameliorate specific conditions within the Sandbox Deployment cloud infrastructure.
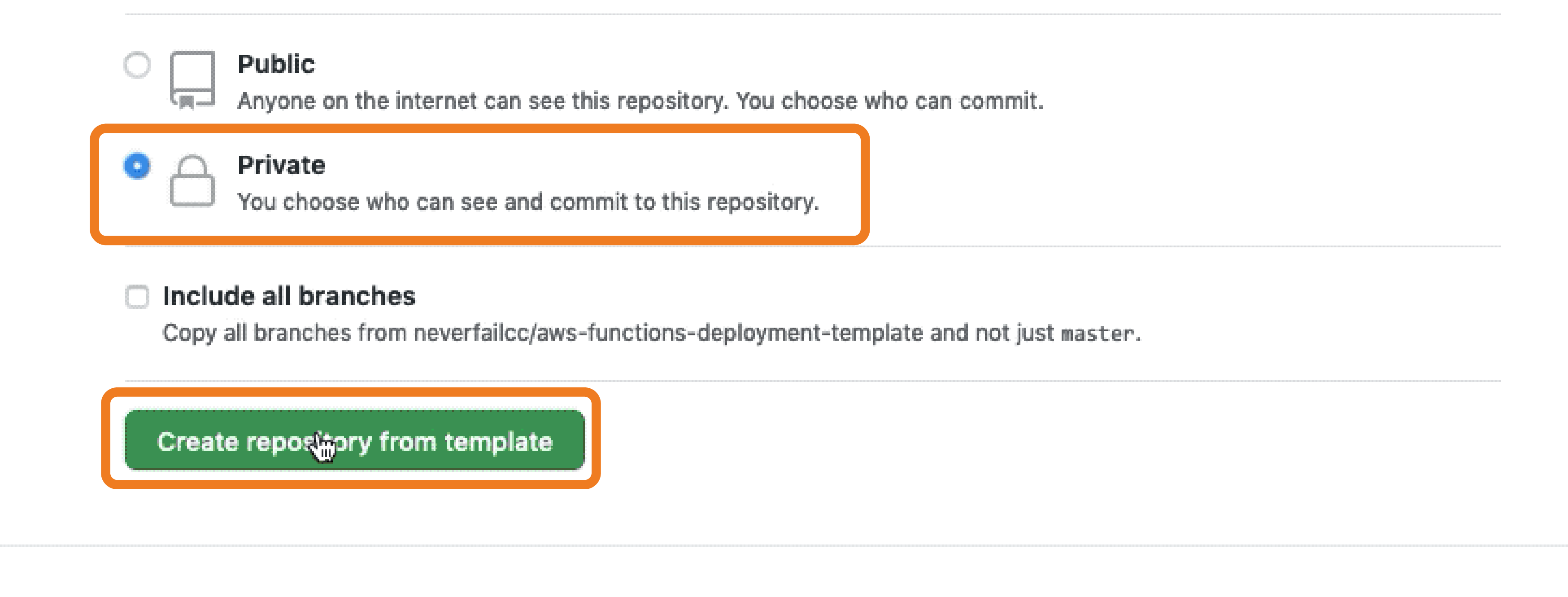
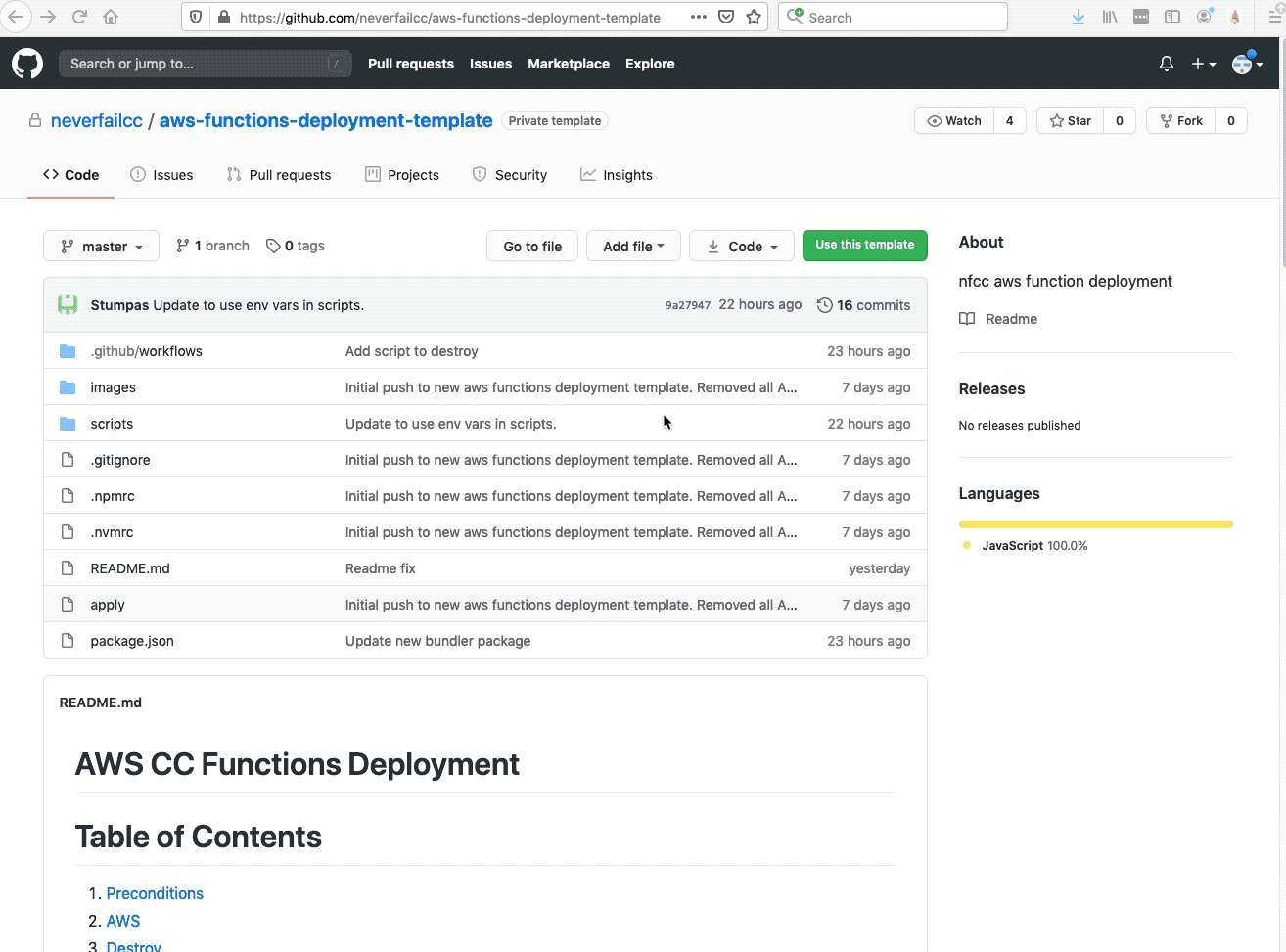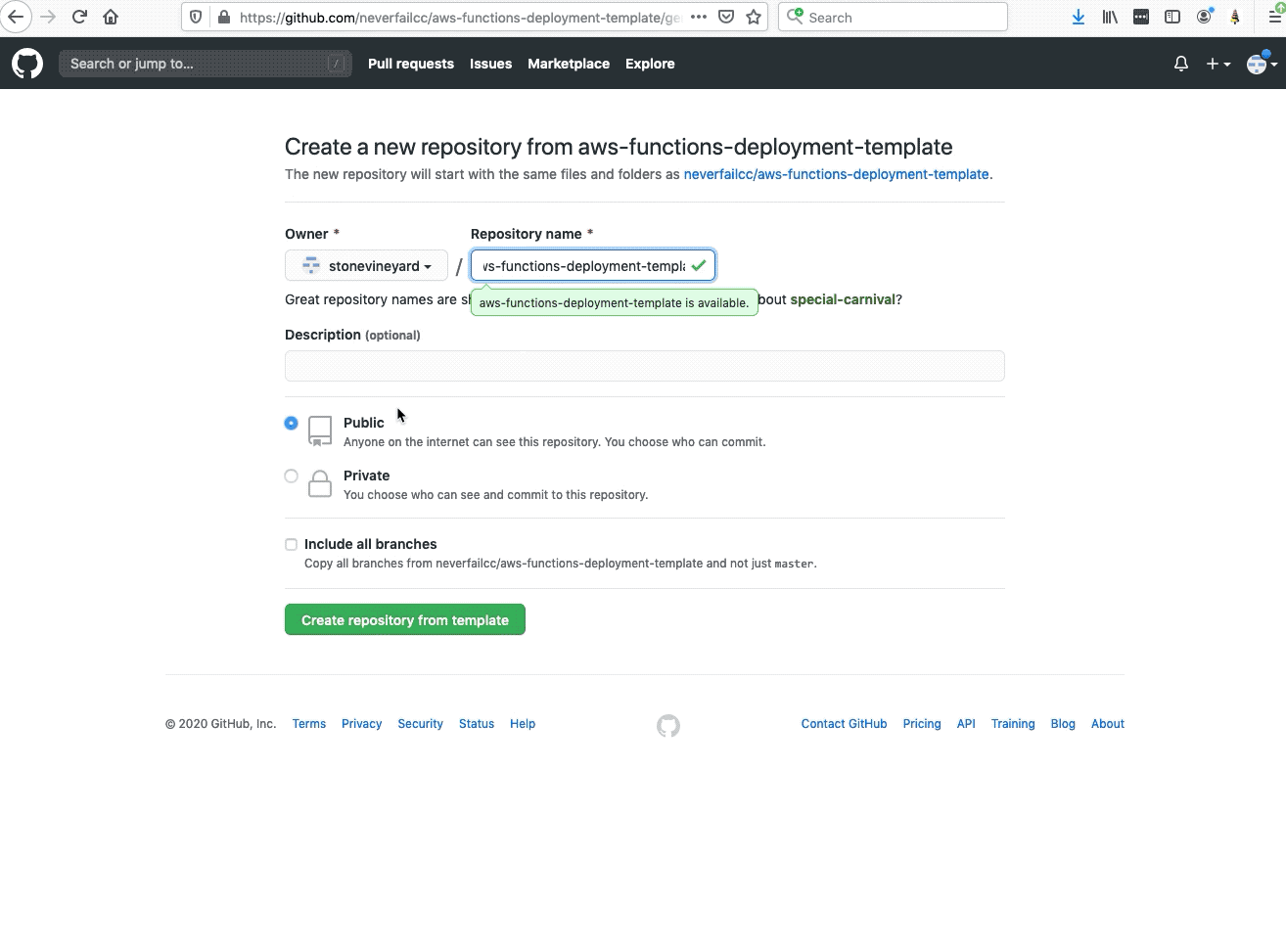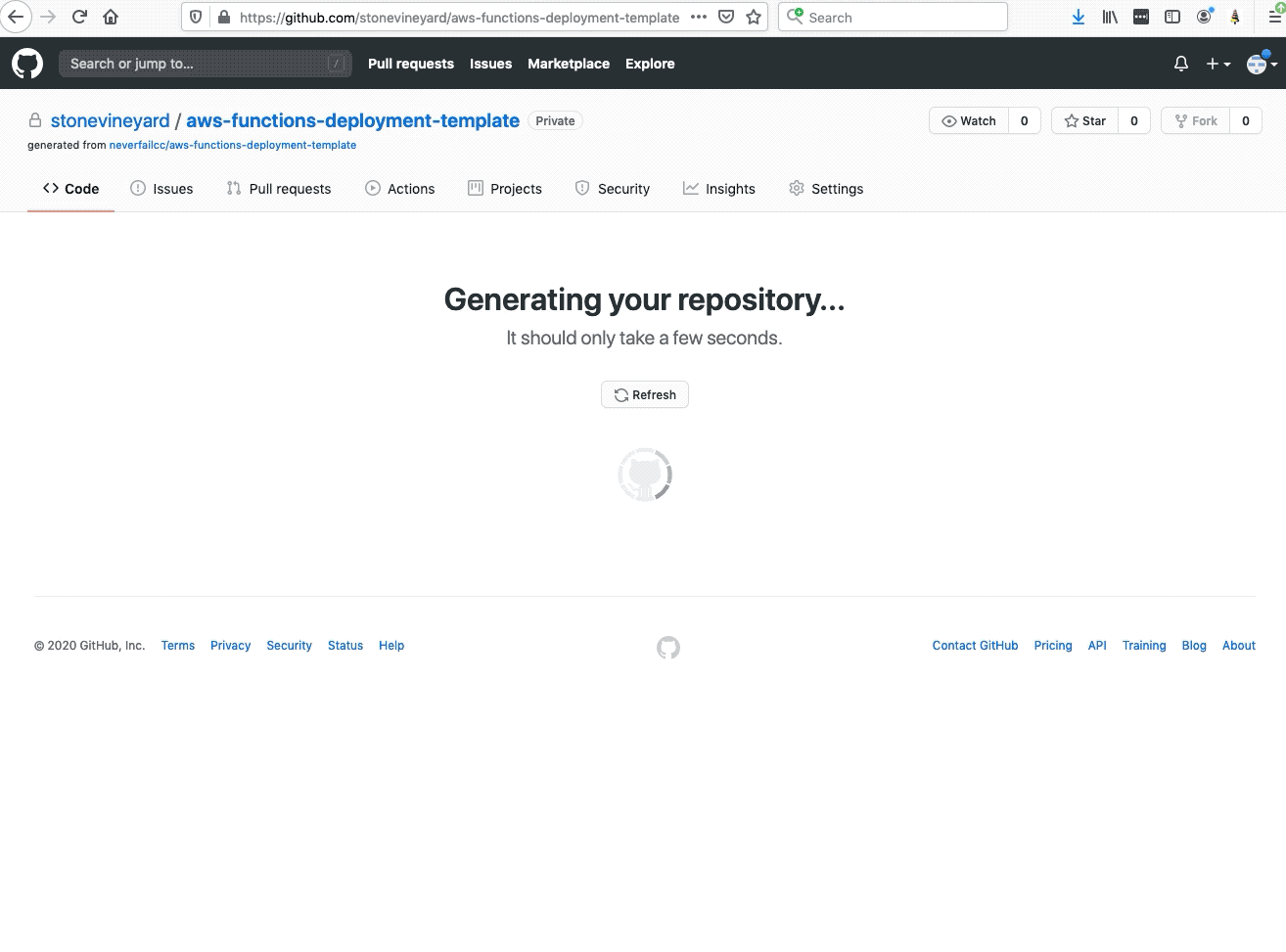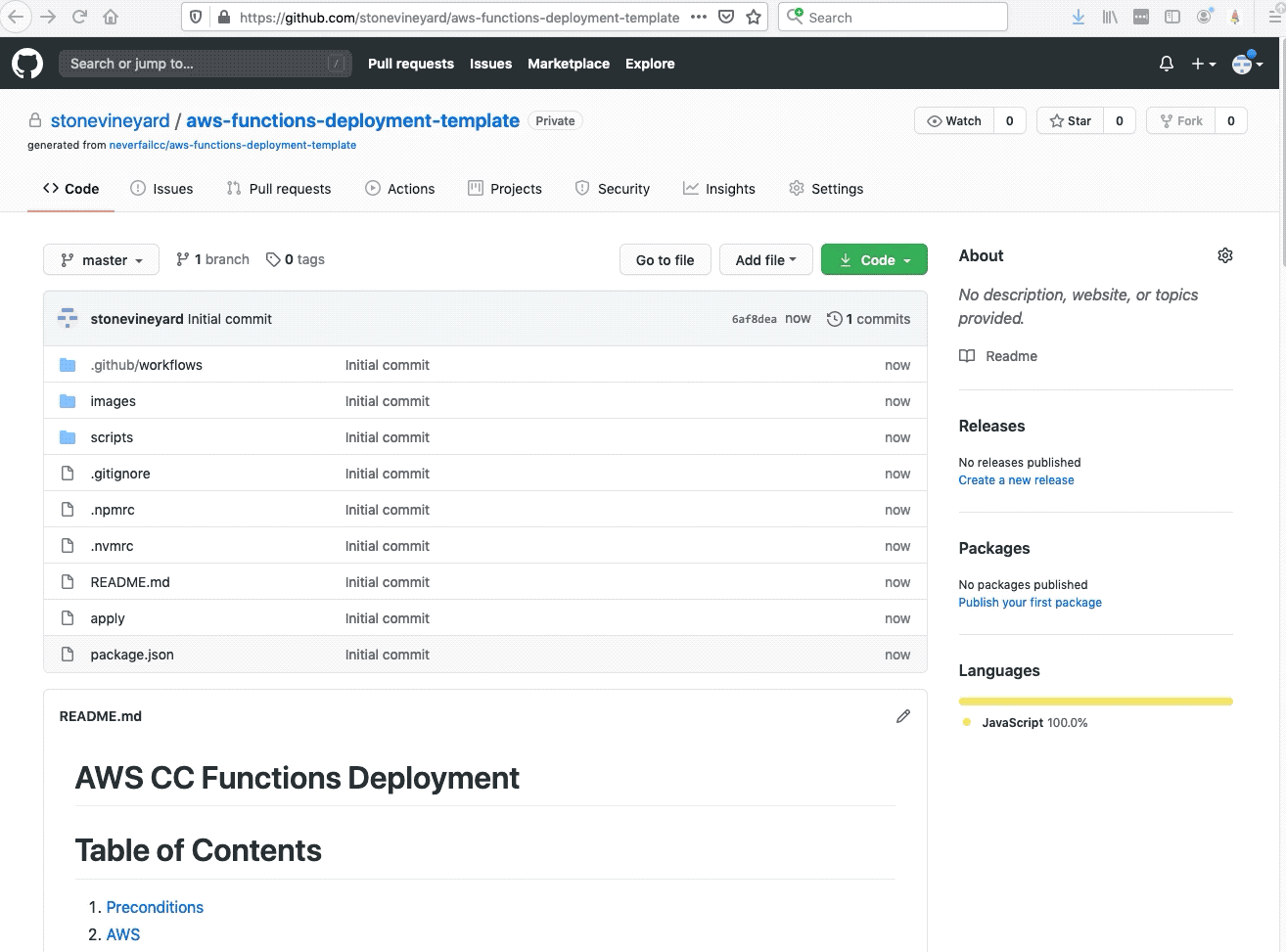
All assets created should have the NFCC-POC : true tag applied. The tags will make it easier to locate resources and to manage billing as tags can be used for spend tracking and budgeting.
The approximate time expected to complete this deployment task is 15 minutes.