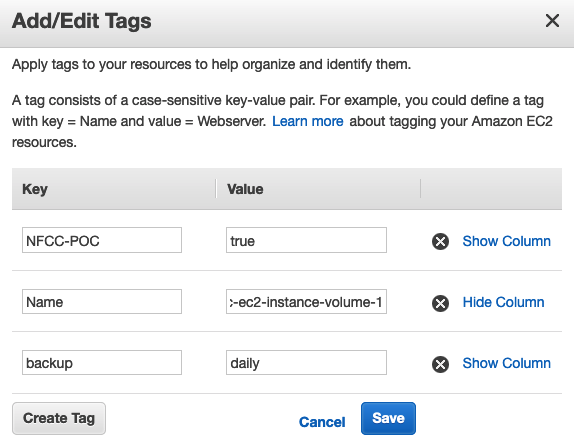
Remediation Bot: Set AWS Backup Plan Policy by Tag
In this case, the remediation bot re-applies a tag to the volume which will add it to a Backup Plan Policy based on the value of this tag. For the purposes of the deployment, the uses the following example tag, but in your real AWS environment, any tag can be configured on a customer-specific basis:
"Key": "backup", "Value": "daily"